| Page 1 out of 13 Pages |
Administrator has recently deployed an NC2 cluster on AWS in the North Virginia region in availability zone
us-east-id. The consuming IPS from a 10.78.2.0/24 range.
The AWS VPC has two available CIDR ranges:
10.78.0.0/16
10.19.101.0/24
The following subnet have been configured in the NC2 AWS VPC: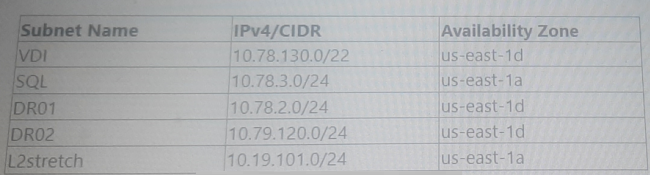
Which two subnet will show up in the Network configuration of the Prism Element Settings page? (Choose
two.)
A. DR01
B. L2stretch
C. VDI
D. DR02
An administrator has deployed an NC2 cluster on AWS to an existing environment for VDI.
Afterwards, the corporate security teams direct the administrator to reuse an existing AWS subnet, 10.79.4.0/24
that has two EC2 instances: EC2-1 (10.79.4.200) and EC2-2 (10.79.4.201). The security team indicates that
this directive is to avoid overlap with the AHV IPAM.
Which two configuration actions should the administrator take to ensure there are no configuration issues?
(Choose two.)
A. aCLI > net.add_to_ip_bfacklist 10.79.4.200 aCLI > net.add_to_ip_blacklist 10.79.4.201
B. Deploy two VMs on the NC2 cluster and assign 10.79.4.200 and 10.79.4.201 as the assigned IPs in Prism Element
C. aCLI > net.de/ete_from_ip_blacklist 10.79.4.200 aCLI > net.defete_fromjp_blacklist 10.79.4.201
D. Configure the AHV JPAM to use DHCP range 10.79.4.2 -10.79.4.253.
A company has a large scale AWS deployment and has just finished installing their first NC2 on AWS
cluster. The new cluster is now running workloads in production.
The cluster is configured with:
* 16 Nodes
* 8 Subnets
* 200 User VMs per subnet
* Nutanix Files
An administrator has been tasked with installing an EC2 instance on one of the subnets that is also used by the
Nutanix, When the EC2 instance is powered on, an IP conflict occurs.
What action should the administrator take to resolve this issue?
A. The IP address used by the NC2 VM should be blocked /excluded from EC2.
B. The Instance Metadata of the NC2 instance needs to have the address reserved.
C. Assign an elastic IP to the EC2 instance and reboot.
D. The IP address used by the EC2 instance should be blocked / excluded from IPAM.
Which two features or services can an administrator ensure are protected by cluster protect within an NC2 environment? (Choose two.)
A. Flow Network Security
B. VM Templates
C. Nutanix Files
D. Virtual Machine Disks
Which service enables the monitoring of key metrics on various AWS services, inducing EC2, EBS, and VPC for an NC2 cluster deployments?
A. Amazon CloudWatch
B. AWS CloudTrail
C. AWS CloudFormation
D. Amazon inspector
An administrator needs to understand which of the services implemented on their NC2 AWS deployment will be protected with Cluster protect. Which service of feature is Cluster Protect able to both protect and recover its associated metadata?
A. Object
B. VM templates
C. Files
D. Categories
| Page 1 out of 13 Pages |