| Page 7 out of 30 Pages |
An administrator needs to shut down an AHV cluster to relocate hardware. The
administrator upgrades NCC and runs health checks.
Which steps should the administrator perform next?
Item instructions: For each procedure, indicate the order in which that procedure must take
place to meet the item requirements.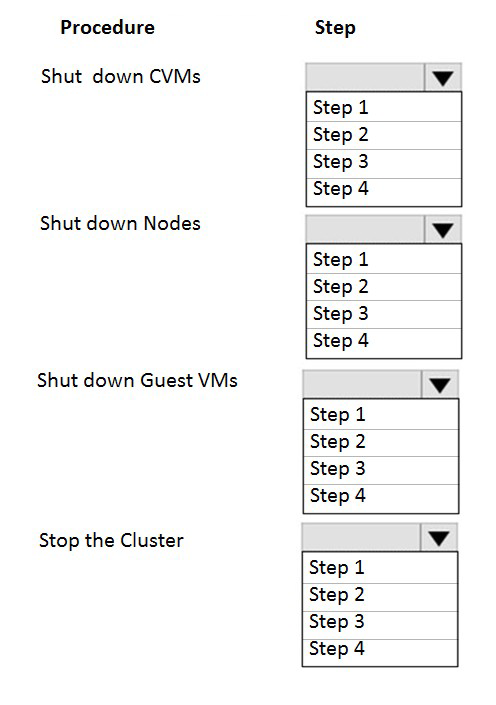
An administrator adds a node with older generation processors to an existing AHV cluster with newer generation processors. What is the effect on live migration?
A. Live migration continues to function as expected and VMs can move to any AHV host.
B. Live migration is prevented until the administrator enables the legacy migration option.
C. Live migration is prevented until the administrator manually changes the newer processor level.
D. Live migration of VMs is prevented between newer and older processors.
Explanation: According to the Migration to a different processor web search result2, live migration of VMs depends on the source and destination hosts having the same CPU functions (CPU flags). Live migration requires the source and destination hosts to have CPUs from the same manufacturer, and only CPU functions which both hosts support are provided (same CPU generation, or by using VMware Enhanced vMotion Compatibility (EVC)). If the administrator adds a node with older generation processors to an existing AHV cluster with newer generation processors, then live migration of VMs is prevented between newer and older processors, unless EVC is enabled.
Refer to Exhibit: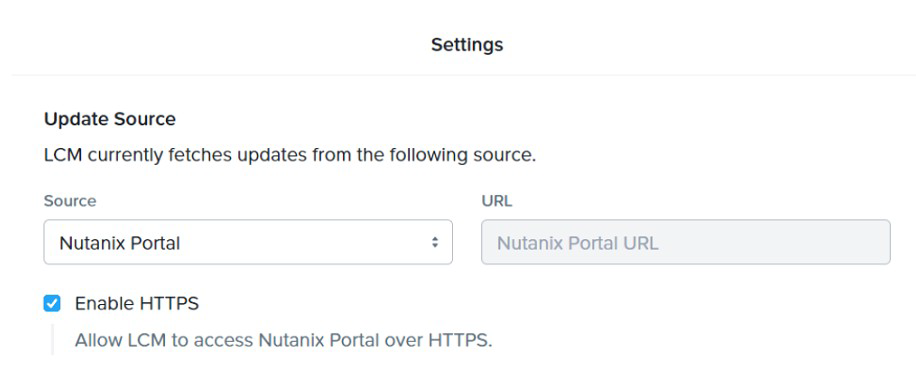
The Update Source for LCM has been configured as shown in the exhibit. Inventory is
failing consistently.
What is the likely cause of this issue?
A. Port 433 Is blocked by a firewall.
B. Port 80 is blocked by a firewall.
C. The administrator does not have a valid portal account.
D. The license assigned to the cluster has expired.
Refer to the exhibit.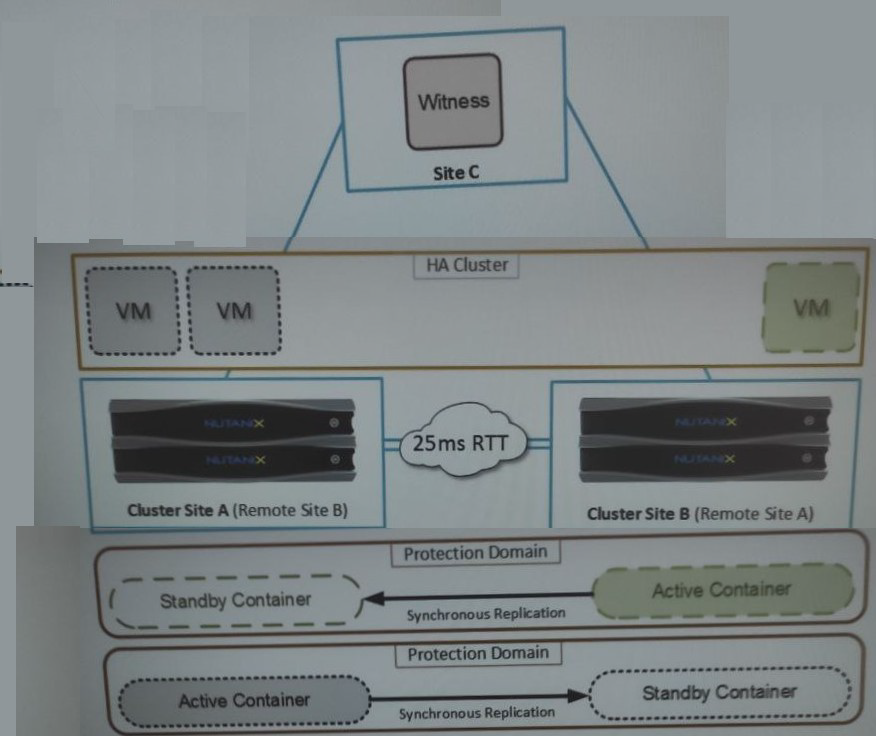
An administrator is trying to implement the solution that is shown in the exhibit, but has
been unsuccessful.
Based on the diagram, what is causing the issue?
A. A remote Witness VM
B. Active containers in both sites
C. Network latency
D. Unsupported hypervisor
Explanation: The correct answer is C. Network latency.
The diagram shows a solution that uses synchronous replication between two remote
protection domains, cluster site A and cluster site B. Synchronous replication is a feature
that allows near-zero RPO (recovery point objective) by replicating data to the remote site
before acknowledging writes to the local site. However, synchronous replication has some
requirements and limitations that must be met for it to work properly. One of these
requirements is that the network latency between the two sites must be less than or equal
to 5 ms1. If the network latency is higher than 5 ms, the synchronous replication will fail
and the protection policy will be suspended2.
Therefore, based on the diagram, the most likely cause of the issue is that the network
latency between cluster site A and cluster site B is higher than 5 ms, which prevents the
synchronous replication from working. To verify this, the administrator can use the “ncli
cluster ping” command to measure the network latency between the two sites3. If the
network latency is indeed higher than 5 ms, the administrator can either improve the
network performance or switch to a different replication mode, such as near-synchronous
or asynchronous.
How many Prism Central instances are required to deploy Leap:'
A. One per availability zone
B. One per customer environment
C. One per physical site
D. One per AHV cluster
Explanation: The number of Prism Central instances required to deploy Leap is one per customer environment. Prism Central is a multi-cluster manager that provides a single, centralized management interface for Nutanix environments3. Leap is a native cloud extension that provides disaster recovery as a service (DRaaS) for Nutanix environments4. To use Leap, customers need to have one Prism Central instance deployed in their primary site, and register it with their Xi Cloud Services account5. This Prism Central instance can manage multiple Nutanix clusters across different physical sites or availability zones6.
Which three configuration scenarios are valid for the deployment of Prism Central? (Choose three.)
A. Environments use Network Address Translation.
B. Prism Elements and Prism Central art in different subnets.
C. Environments do not have Internet access.
D. Prism Elements and Prism Central have proxy configured.
E. Environments use the 192.168.5.0/24 CVM management network.
Explanation: Prism Central is a multi-cluster manager that provides a single, centralized
management interface for Nutanix environments1. Prism Central can be deployed in
different configuration scenarios, depending on the network and security requirements of
the environment. Some of the valid scenarios are:
Environments use Network Address Translation (NAT): NAT is a method of
mapping one IP address space to another by modifying network address
information in IP datagram packet headers while they are in transit across a traffic
routing device2. NAT can be used to enable communication between Prism
Central and Prism Elements that are in different networks or subnets3. For
example, Prism Central can be deployed in a public cloud and use NAT to access
Prism Elements that are in a private data center3.
Prism Elements and Prism Central are in different subnets: A subnet is a logical
subdivision of an IP network that allows multiple networks to share a single
physical network4. Prism Elements and Prism Central can be in different subnets
as long as they can communicate with each other through routing or NAT3. For
example, Prism Central can be deployed in a management subnet and access
Prism Elements that are in different application subnets3.
Environments do not have Internet access: Internet access is not required for the
deployment of Prism Central, as long as the environment meets the prerequisites
and considerations for installing or upgrading Prism Central. For example, Prism
Central can be deployed in a dark site, which is an environment that does not have
Internet access or has restricted Internet access. In this case, the administrator
needs to manually enable microservices infrastructure and download the required
software packages from another source.
| Page 7 out of 30 Pages |
| Nutanix NCP-MCI-6.5 Practice Questions Home | Previous |