| Page 9 out of 30 Pages |
Which node type does not deploy a Nutanix Controller VM?
A. Storage Only
B. Hyper Converged
C. Compute Only
D. All Flash
Explanation: A Compute Only node is a node that does not have any local storage devices and only provides compute resources to the cluster2. A Compute Only node does not run a CVM, but instead relies on the CVMs of other nodes to access the distributed storage fabric2.
An administrator logs in to Prism Element goes to the Network view, and sees the output
shown in the exhibit.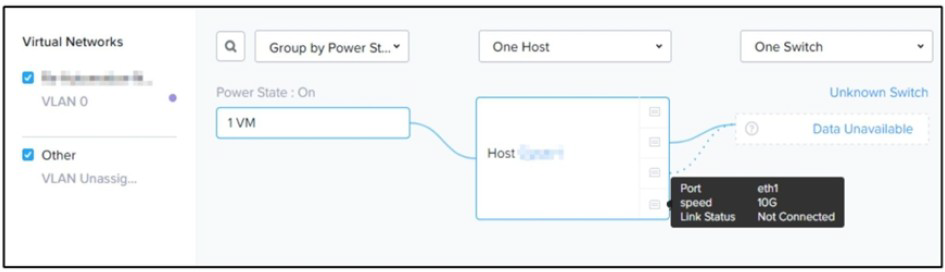
Which three steps must the administrator take to increase throughput to the host? (Choose
three.)
A. Connect the 10Gb interfaces to the physical switch
B. Change the bond mode to balance-slb or balance—tcp.
C. Remove any 1Gb interfaces still connected from the default bond.
D. Add a new switch to the network and connect 1Gb interfaces to it
E. Change the VLAN ID to a higher priority ID.
Explanation: These are the three steps that the administrator must take to increase
throughput to the host. According to the network diagram, the host has two 10Gb interfaces
and two 1Gb interfaces in the default bond, but only one of the 10Gb interfaces is
connected to a switch. The other 10Gb interface is disconnected and has a red “X” on it.
The two 1Gb interfaces are also disconnected and have dotted lines. This means that the
host is using only one 10Gb interface for all its network traffic, which limits its maximum
bandwidth to 10 Gbps.
To increase the throughput, the administrator should connect both 10Gb interfaces to the
physical switch, preferably to different switches for redundancy and high availability. This
will allow the host to use both 10Gb interfaces for network traffic, which can increase its
maximum bandwidth to 20 Gbps. However, this also requires changing the bond mode
from active-backup to balance-slb or balance-tcp, which are load balancing modes that
distribute network traffic across multiple interfaces based on source MAC address or TCP
session1. The default bond mode of active-backup only uses one interface at a time and
switches to another interface only when the active one fails2.
Finally, the administrator should remove any 1Gb interfaces still connected from the default
bond, as they are not needed and may cause performance issues or conflicts with the load
balancing modes. The 1Gb interfaces can be used for other purposes, such as
management or backup networks, by creating separate bonds or bridges for them3.
Alternatively, they can be left disconnected if they are not required.
An administrator is working with Nutanix Support and needs to provide logs for troubleshooting an issue. The cluster is located in a secure environment. Data such as IP addresses and VM names cannot be shared. Which method should be used to anonymize the log data sent to Nutanix Support?
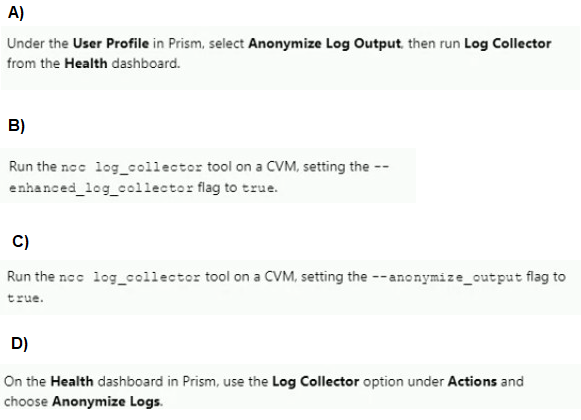
A. Option A
B. Option B
C. Option C
D. Option D
An administrator wants to create a trunked interface on a VM on AOS 5.15x. Which two steps should the administrator take first to achieve this? (Choose two)
A. Use acli
B. Log in over PE web UI.
C. SSH to CVM.
D. Update VM dialog.
In the event of a disk failure, which process will immediately ad automatically scans Cassandra to find all data previously hosted on the failed disk, and all disks in that node?
A. Curator
B. Stargate
C. Genesis
D. Prism
Explanation: Curator is the process that runs on every node in a Nutanix cluster and is responsible for data management tasks such as deduplication, compression, erasure coding, and replication factor compliance. Curator also handles disk failure recovery by scanning Cassandra to find all data previously hosted on the failed disk, and all disks in that node. Curator then rebuilds the data on other nodes in the cluster using the distributed storage fabric1.
Refer to Exhibit: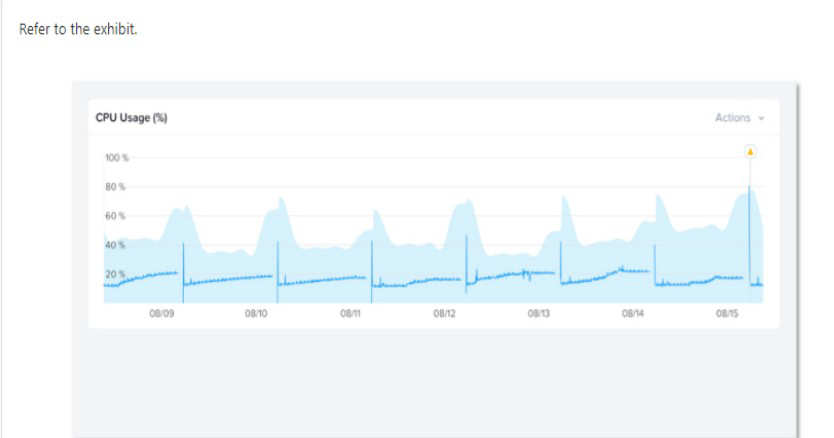
Why has an anomaly been triggered?
A. Because the CPU usage crossed the blue band.
B. Because the blue band range increased over the last 2 days
C. Because the CPU usage dropped belon' 20%
D. Because the CPU usage reached 100%
Explanation: Nutanix leverages a method for determining the bands called ‘Generalized
Extreme Studentized Deviate Test’. A simple way to think about this is similar to a
confidence interval where the values are between the lower and upper limits established by
the algorithm.
Another web source3 shows an example of how anomaly detection works in Nutanix Prism Central. In the video, you can see that when the observed value of a metric deviates
significantly from the predicted value based on historical data, an anomaly event is
triggered and displayed on a chart.
Therefore, by comparing the observed values with the predicted values based on historical
data, Nutanix anomaly detection can identify abnormal behavior and alert you accordingly.
| Page 9 out of 30 Pages |
| Nutanix NCP-MCI-6.5 Practice Questions Home | Previous |